Moodle SQL Injection Vulnerability
A security vulnerability in e-learning platform Moodle could allow an attacker to take over a database and potentially obtain sensitive information, researchers have warned
Moodle is an open source educational resource that enables institutions to create online learning materials for students.
Researchers have found that the website is vulnerable to a second order SQL injection flaw, which could enable an attacker to potentially take control of a database server.
Teachers are able to create custom badges for their pupils, which they can earn through completing tasks such as courses or essays.
When creating these badges, it is possible for an attacker with teacher status to insert a malicious SQL query into the database.
Later, that data is fetched from the database and is injected unsanitized into another query. When the badge is enabled for access by students, the injected SQL query will be executed.
In a blog post, researcher ‘dugisec’ explained how the attack works.
Caveats
It’s important to note that in order to perform this attack, a malicious actor will have to be logged in as a teacher.
However, the impact of the authenticated bug could be damaging. The researcher who found the vulnerability said it can also be used in a stored XSS attack.
They wrote: “In order to exploit this, a new badge has to be created for each SQL query that the attacker wants to run. This is because once a badge has been created, the criteria cannot be updated.”
The researcher added: “I also would not be surprised if there are more SQLis of this nature in Moodle. As a bonus this bug can be used for stored XSS as well.”
The researcher noted that this bug appears to have been reported in a GitHub post from 2013.
The report reads: “In order to get our SQL query into the database it’s necessary to create a badge and add some criteria. It is when adding the critera that the sql-to-be-executed-2nd-order is inserted into the database.
“Finally, when the badge is enabled the injected SQL is executed.”
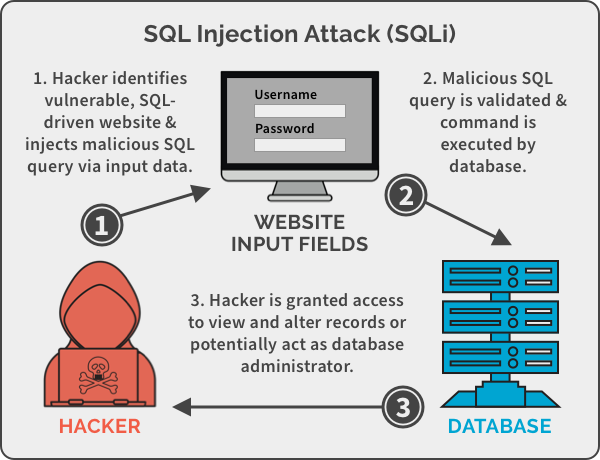
What is an SQL Injection Vulnerability?
SQL injection is a web security vulnerability that allows an attacker to interfere with the queries that an application makes to its database.
Go to Cybersecurity Knowledge Base
Stay informed of the latest Cybersecurity trends, threats and developments. Sign up for RiSec Weekly Cybersecurity Newsletter Today
Remember, CyberSecurity Starts With You!
- Globally, 30,000 websites are hacked daily.
- 64% of companies worldwide have experienced at least one form of a cyber attack.
- There were 20M breached records in March 2021.
- In 2020, ransomware cases grew by 150%.
- Email is responsible for around 94% of all malware.
- Every 39 seconds, there is a new attack somewhere on the web.
- An average of around 24,000 malicious mobile apps are blocked daily on the internet.




