Crypto-Locking Malware Hits Traced by Microsoft to Attack Group Based in China
Attackers wielding Night Sky ransomware are among the latest groups that have been attempting to exploit serious vulnerabilities in widely used Apache Log4j software.
“In January, we started seeing attackers taking advantage of the vulnerabilities in internet-facing systems, eventually deploying ransomware,” Microsoft says. “We have observed many existing attackers adding exploits of these vulnerabilities in their existing malware kits and tactics, from coin miners to hands-on-keyboard attacks. Organizations may not realize their environments may already be compromised.”
The emergence of ransomware-wielding attackers targeting Log4j vulnerabilities came just weeks after Apache’s first public alert, on Dec. 10, 2021, that a critical flaw in the Java Naming and Directory Interface API, in versions of the Log4j logging utility prior to 2.15.0, could be exploited to take control of a vulnerable system.
There are now a total of three such “Log4Shell” vulnerabilities: CVE-2021-44228 (the JNDI flaw in Log4j 2.x), CVE-2021-4104 (for how that vulnerability presents in certain uses of Log4j 1.x) and CVE-2021-45046 (a vulnerability introduced via an incomplete fix for the JNDI flaw). All have been patched via updates to Log4j, which have also included fixes for other newly discovered but less severe flaws.
As of Wednesday, the latest version of Log4j continues to be 2.17.1.

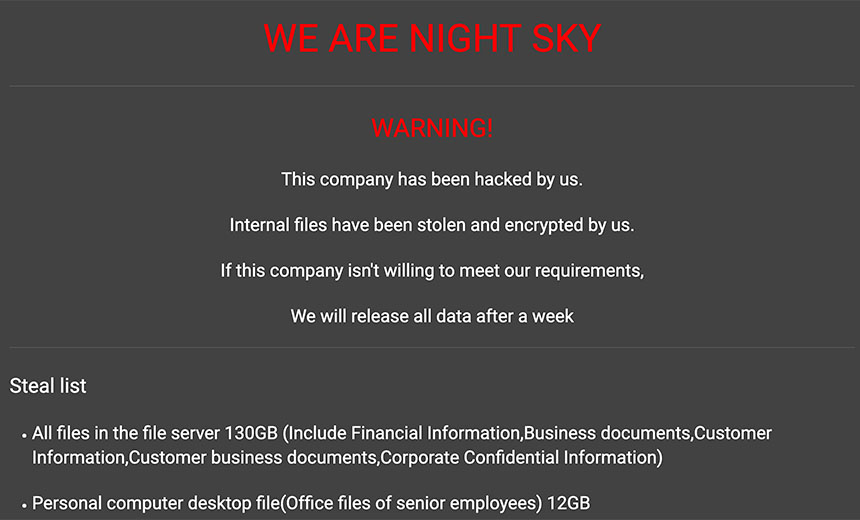
Night Sky Ransomware
The Night Sky crypto-locking malware being distributed by attackers gets installed when they exploit Log4j flaws in unpatched versions of VMware Horizon, Microsoft says.
The Night Sky ransomware attacks followed a Dec. 23, 2021, security alert from VMware warning that CVE-2021-44228 and CVE-2021-45046 were present in VMware Horizon and the VMware Horizon Agent that runs on-premises. That alert included mitigation recommendations.
Night Sky ransomware appears to be new. It was first spotted by security research group MalwareHunterTeam, which on Jan. 1 reported finding a dedicated data leak site for attacks tied to that strain of ransomware. As such, it means the attackers are practicing double extortion, meaning they demand payment not just for a decryptor, but also to not release stolen data.
MalwareHunterTeam reports that on Dec. 27, 2021, “the support chat system was set up – both the domain and the system itself” for Night Sky victims, while posts announcing two victims – one in Bangladesh and another in Japan – were added to the site on each of the two next days. Each of those victim listings includes samples of supposedly stolen data. It’s not clear how Night Sky ransomware was dropped on those two victims’ systems.
One of the Night Sky victims received a ransom demand of $800,000, in return for which the attackers agreed to furnish a decryptor as well as not dump stolen data, Bleeping Computer reported.
China-Based Attackers
But the attackers began targeting VMware Horizon no more than 10 days after VMware issued its security alert. “As early as Jan. 4, attackers started exploiting the CVE-2021-44228 vulnerability in internet-facing systems running VMware Horizon,” Microsoft says.
“These attacks are performed by a China-based ransomware operator that we’re tracking as DEV-0401,” it adds. This attack group “has previously deployed multiple ransomware families including LockFile, AtomSilo and Rook, and has similarly exploited internet-facing systems running Confluence (CVE-2021-26084) and on-premises Exchange servers (CVE-2021-34473).”
As part of its attacks, the DEV-0401 group uses spoofed domain names that are meant to look legitimate but that typically feature slight misspellings, Microsoft says. Examples include “service[.]trendmrcio[.]com,” “api[.]rogerscorp[.]org,” “api[.]sophosantivirus[.]ga” and “apicon[.]nvidialab[.]us,” among others.
Escalating Attack Attempts
Last week, the U.K.’s National Health Service issued a security alert warning that attackers had been compromising VMware Horizon to gain persistence on NHS systems. The alert did not attribute those attacks to any particular group.
The Log4j flaw has allegedly also been used to drop ransomware into the IT environment at ONUS, which is one of Vietnam’s largest cryptocurrency platforms.
Getting hit with ransomware is just one of the risks facing organizations that use tools in which the vulnerable Log4j code is present. And the U.S. Cybersecurity and Infrastructure Security Agency says hundreds of millions of devices worldwide likely still run one of hundreds of pieces of software that contain vulnerable Log4j software.
As Britain’s National Cyber Security Center has said: ” If left unfixed, attackers can break into systems, steal passwords and logins, extract data and infect networks with malicious software.”
So far, however, CISA reports seeing largely low-level attacks targeting Log4j, primarily aimed at building botnets or mining for cryptocurrency. But on Monday, CISA Director Jen Easterly warned that more advanced attackers may have already been exploiting the flaw to gain persistence and lie low on systems until defenders are at a “lower alert” level.
Indeed, security researchers say nation-state attackers have also been searching for the flaw. Last month, Belgium’s Ministry of Defense announced that it had been hit by an attacker that utilized, in part, the Apache Log4j vulnerability.
Another example comes via software and hardware vendor Check Point, which reports that an advanced persistent threat group with the codenames APT35, Charming Kitten, Phosphorus and TA453, which is believed to be tied to Iran, “started widespread scanning and attempts to leverage Log4j flaw in publicly facing systems only four days after the vulnerability was disclosed.”
If the group’s Log4j exploit is successful, Check Point says the attackers switch to a PowerShell-based framework they’ve developed “to establish persistence, gather information and execute commands.” The vendor didn’t disclose how many organizations may yet have been successfully exploited in this manner.
Separately, cybersecurity firm CrowdStrike in late December warned that a China-linked espionage group, with the codename Aquatic Panda, had targeted a “large academic institution,” attempting to exploit the Apache Log4j flaw in the VMware Horizon Tomcat web server service. But CrowdStrike said that attack had been repelled.
Serious Patching Challenge
Meanwhile, Log4j challenges continue, including for vendors that remain in the process of having to identify and patch vulnerable software and systems. Then their customers and users will have to test these updates and release them into their own environments.
The challenge is compounded because many vulnerable products and services are in turn used by other products and services. “This open-source component is widely used across many suppliers’ software and services,” Microsoft says. “By nature of Log4j being a component, the vulnerabilities affect not only applications that use vulnerable libraries, but also any services that use these applications, so customers may not readily know how widespread the issue is in their environment.”
On Monday, Easterly said that CISA has cataloged more than 2,800 products that are known to be vulnerable to Log4Shell. The agency is tracking vulnerable products in a dedicated GitHub database.
A separate effort by the CERT Coordination Center, run by Carnegie Mellon University’s Software Engineering Institute, is tracking the presence or absence of the critical Log4j flaws across products issued by more than 1,600 vendors.
In response to CERT CC’s queries, 122 vendors have confirmed that they have one or more products or services affected by one of the three Log4j flaws. In addition, 91 vendors have responded saying none of their products or services are affected. But more than 1,400 vendors have yet to confirm or deny if their products or services run a vulnerable version of Log4j. At the same time, would-be attackers have access to numerous tools to help them identify systems with such flaws.
“Customers should assume broad availability of exploit code and scanning capabilities to be a real and present danger to their environments,” Microsoft says. “Due to the many software and services that are impacted and given the pace of updates, this is expected to have a long tail for remediation, requiring ongoing, sustainable vigilance.”#
Continue reading more cybersecurity articles