Threat actors are actively incorporating public cloud services from Amazon and Microsoft into their malicious campaigns to deliver commodity remote access trojans (RATs) such as Nanocore, Netwire, and AsyncRAT to siphon sensitive information from compromised systems.
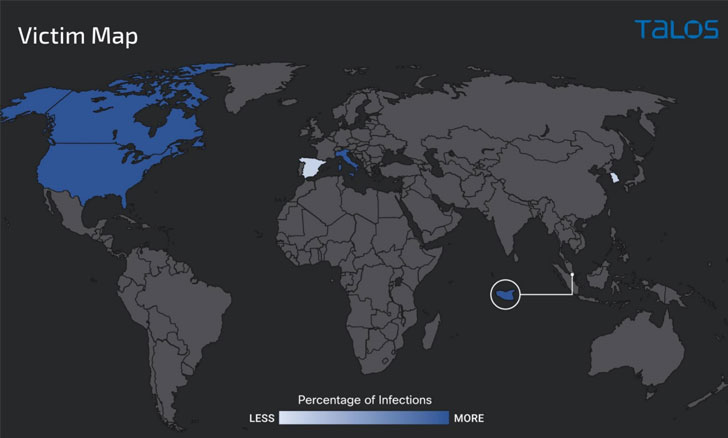
The spear-phishing attacks, which commenced in October 2021, have primarily targeted entities located in the U.S., Canada, Italy, and Singapore, researchers from Cisco Talos said in a report shared with THN
Using existing infrastructure to facilitate intrusions is increasingly becoming part of an attacker’s playbook as it obviates the need to host their own servers, not to mention using it as a cloaking mechanism to evade detection by security solutions.
In recent months, collaboration and communication tools like Discord, Slack, and Telegram have found a place in many an infection chain to commandeer and exfiltrate data from the victim machines. Viewed in that light, the abuse of cloud platforms is a tactical extension that attackers could exploit as a first step into a vast array of networks.
“There are several interesting aspects to this particular campaign, and it points to some of the things we commonly see used and abused by malicious actors,” Nick Biasini, head of outreach at Cisco Talos, told The Hacker News via email.
“From the use of cloud infrastructure to host malware to the abuse of dynamic DNS for command-and-control (C2) activities. Additionally, the layers of obfuscation point to the current state of criminal cyber activities, where it takes lots of analysis to get down to the final payload and intentions of the attack.”
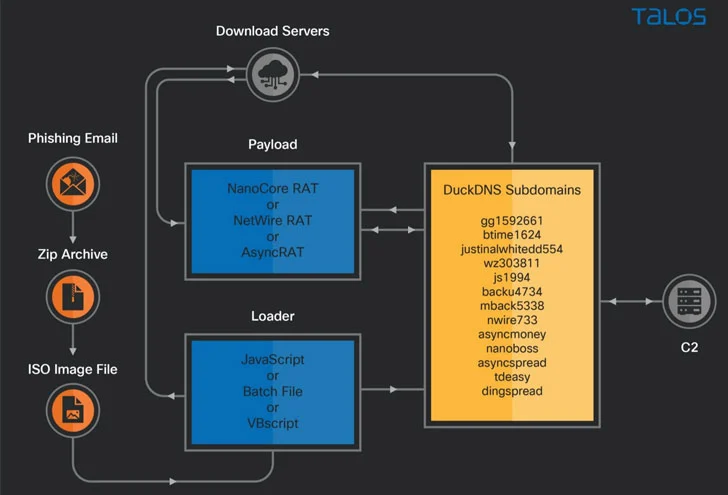
As with many of these types of campaigns, it all starts with an invoice-themed phishing email containing a ZIP file attachment that, when opened, triggers an attack sequence that downloads next-stage payloads hosted on an Azure Cloud-based Windows server or an AWS EC2 instance, ultimately culminating in the deployment of different RATs, including AsyncRAT, Nanocore, and Netwire.
Also noteworthy is the use of DuckDNS, a free dynamic DNS service, to create malicious subdomains to deliver malware, with some of the actor-controlled malicious subdomains resolving to the download server on Azure Cloud while other servers are operated as C2 for the RAT payloads.
“Malicious actors are opportunistic and will always be looking for new and inventive ways to both host malware and infect victims,” Biasini said. “The abuse of platforms such as Slack and Discord as well as the related cloud abuse are part of this pattern. We also commonly find compromised websites being used to host malware and other infrastructure as well and again points to the fact that these adversaries will use any and all means to compromise victims.”
We think you may enjoy reading, Steps to Hardening your VPS Security




