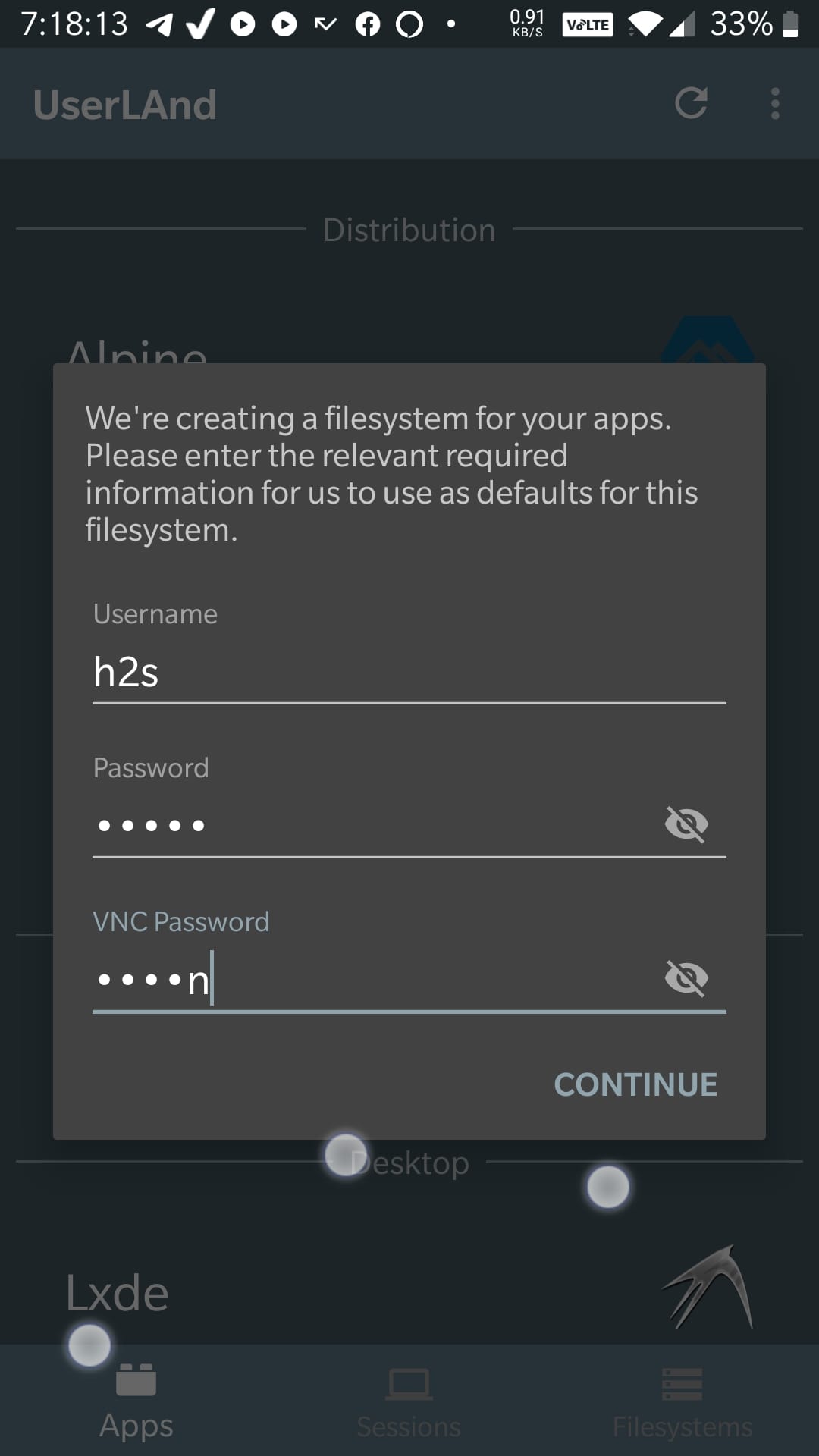
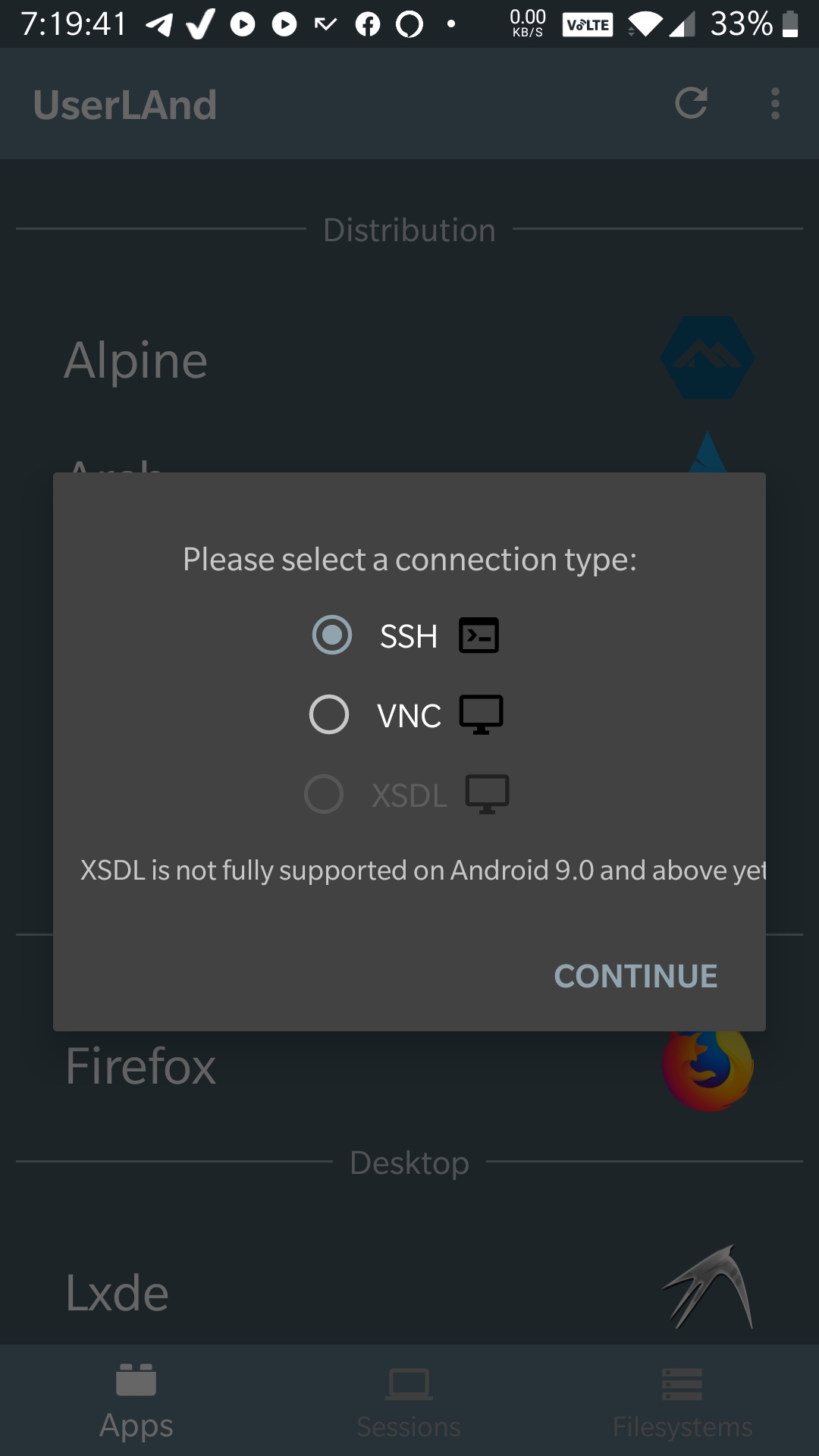
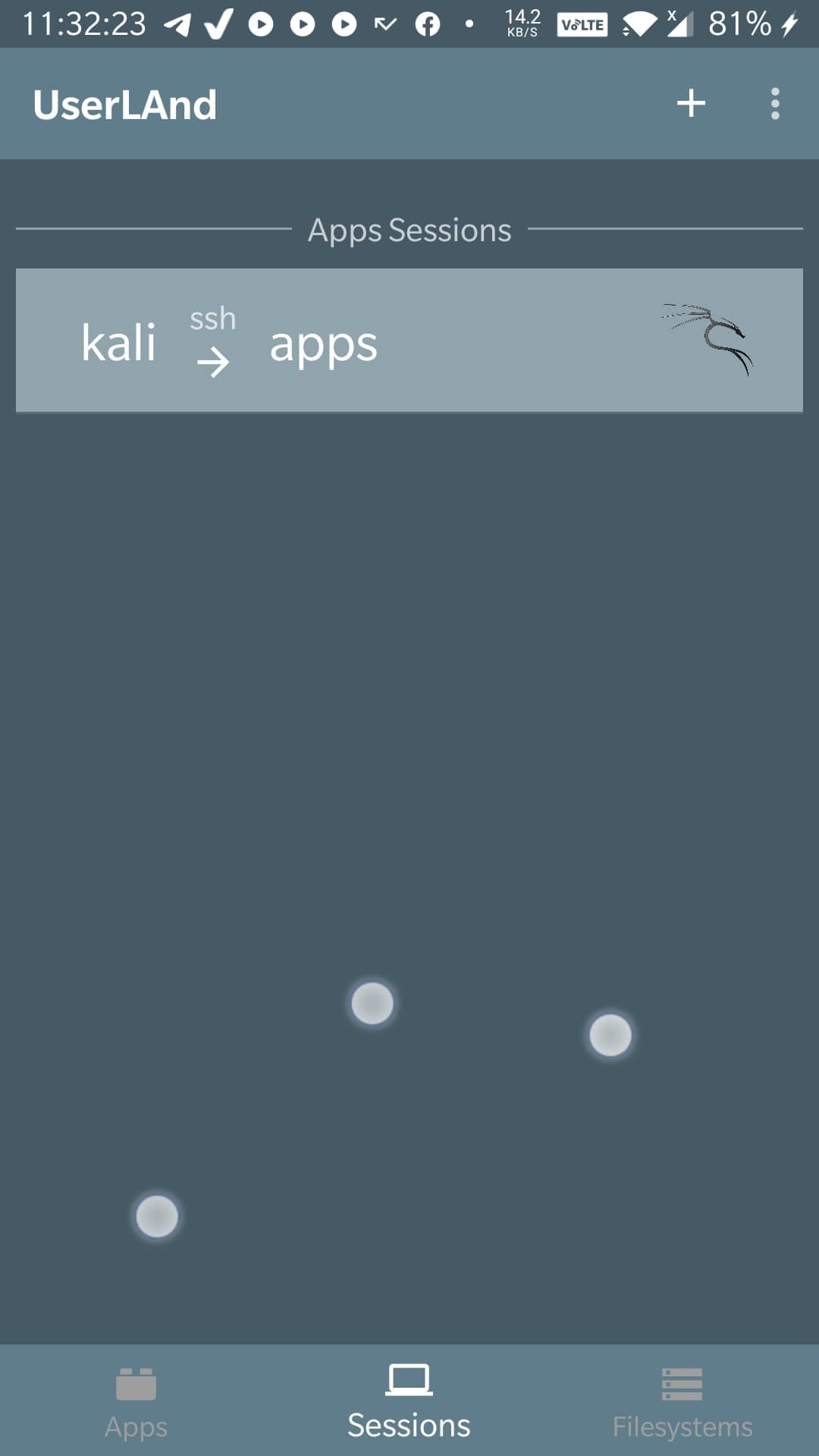
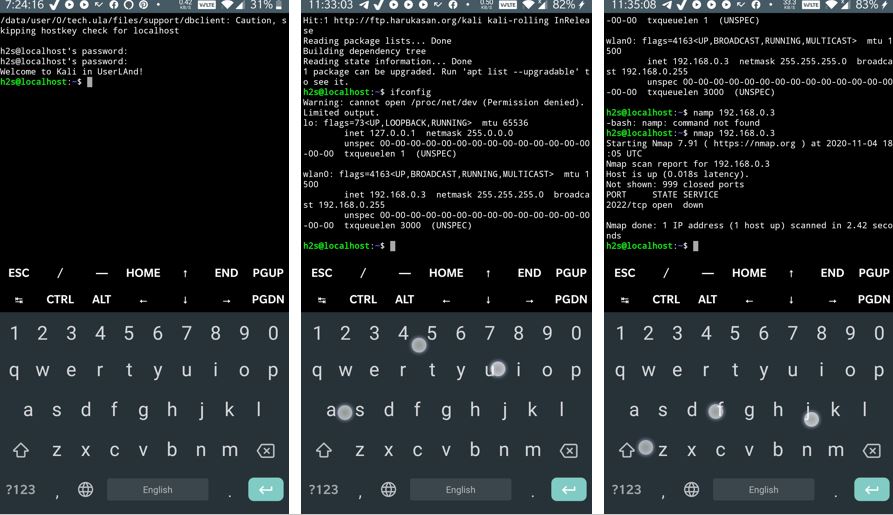
IoT
In the Internet of Things (IoT) settings, objects are linked on a network to share data, but a number of these IoT systems are built and implemented with inadequate security in mind. Consequently, these systems have increasingly become a target of various attacks. An effective solution for guaranteeing the security and safety of a network system is through penetration testing.
In general, penetration testing is implemented to identify the vulnerabilities or potential attacks on traditional systems. A quick fix of these vulnerabilities can mitigate future attacks. However, IoT penetration testing is far from being a wide practice. IoT penetration testing aims to uncover all viable methods an attacker can employ to breach the target system through target-graphs.
By implementing a layered methodology, where every single layer is evaluated, penetration testers can identify vulnerabilities that may have been overlooked. The benefits of penetration testing for IoT systems are numerous. IoT pen-tests reduce the risk of compromise, fortify device security, promote better user and data privacy, safeguards against unauthorized usage, and set strong encryption to prevent man-in-the-middle (MTM) attacks prevents Elevation of Privileges.
What Are the Attack Surface Areas of IoT?
An IoT attack surface is the combination of all prospective security weaknesses in IoT devices and related systems. The following are the IoT attack surface areas:
Applications, Firmware, and Software
The Vulnerabilities present in web-based applications and other associated software for IoT systems can result in compromised systems. For instance, web applications can be manipulated to boost malicious firmware updates or steal sensitive user credentials.
Embedded Devices
Attackers usually use devices as their central approach for launching attacks. Embedded devices in IoT systems can be employed for various functions depending on the user case scenario. Some parts of a device are vulnerable to attacks, including network services, firmware, memory, web interface, and physical interface.
Malicious actors can also exploit other vulnerabilities like outdated components, unsecured default settings, and unsecured update mechanisms. Some vulnerabilities found with embedded devices include
- Insecure authentication system employed in serial ports
- Exposed serial ports
- Power analysis and side channel-based attacks
- External media-based attacks
Communication Channels
Likewise, attacks can start in the channels that link the IoT components together. Several different radio communications protocols can be employed, including Wi-Fi, cellular, BLE, wave, etc. Also, IoT devices can be prone to known network attacks and vulnerabilities present in communication channels, including:
- Spoofing
- Jamming-based attacks
- Denial of Service (DoS) attacks
- Man-in-the-middle attacks
- Live radio communication interception and modification
- Replay-based attacks
If you have only been working in flat networks, EC-Council’s Certified Penetration Testing Professional or CPENT training program will help you take your skills to the next level by teaching you to pen-test IoT systems and OT systems, among others.
Common Attacks in IoT Systems
The following are the most common attacks in IoT systems hat organizations need to design a comprehensive approach to cybersecurity to protect themselves from known and unknown attacks:
- Ransomware
- Botnets
- Advanced persistent threats
- Denial of service (DoS) attacks and Distributed Denial of Service (DDoS) attacks
- Identity and data theft
- Spamming and phishing
- Man-in-the-Middle attacks
- Social engineering attacks
- Remote recording
How to Secure the IoT?
Given that any part of the IoT system can be compromised, you must prioritize developing and maintaining secured IoT systems. Notwithstanding your organization’s size, security measures should be implemented from the design phase to incorporate it into every part of the system.
Physical Security Is Crucial
You probably don’t consider physical security when thinking about IoT pentesting. However, physical security is your first line of defense against potential security attacks. Thus, you should ensure that each of your physical assets is properly secured. Penetration testers should conduct expert social engineering and physical security tests to detect vulnerabilities that organizations may have ignored.
Threat Modeling
It is an open secret that IoT devices usually fall behind when it comes to information and data security. This is why you need to incorporate threat modeling processes during your IoT pentesting. The basic threats you’ll encounter and mitigate in an architecturally-centric threat modeling are Denial of Service, denial hijack, action spoofing, faking the data source, and alteration of installed BIOS, among others.
Hardware and Firmware-Focused Security Solutions
One way or the other you’ll get the firmware. Firmware can be decompiled and assessed dynamically or manually to gain critical insights into the device’s nature. When this is accompanied by penetration testing, the information gathered may offer active insights that can help the pentester locate a bug in the code. Some of the widespread bugs to search for on hardware devices include
- Abuse of diagnostic utilities (e.g. tcpdump)
- Absence of hardware correct device hardening
- CLI injection
- Absence of appropriate user rights assignments
- Initial boot-up: if the device has a recovery code or if it’s possible to disrupt the initial boot up.
- Web-based: Forced browsing/XSS/SSRF/CSRF
- Inappropriate handling and delegation of default admin/root credentials
Spend just 40-hours and align your career to the growing demand for Penetration testers! Enroll for the CPENT to learn more about the most significant advanced penetration testing tools, methodologies, and techniques today.
The Need for IoT Penetration Testing
IoT pentesting evaluates and exploits numerous components available in an IoT device solution to render the device more secure. An IoT pentesting usually begins with mapping the whole attack surface of the solution. This is supported by pinpointing vulnerabilities and executing exploitation, which is later accompanied by post-exploitation. The IoT pentesting process is then completed with a detailed technical report.
According to Gartner, about 20 billion IoT devices will be available by 2020. This does not include “general purpose” devices such as smartphones, but rather committed, physical items that include embedded technology to detect or interact with the external environment or their internal state. Given the rise in IoT systems, there are endless possibilities for IoT usages. You can save energy, time, money, and even lives using IoT systems.
However, the flip side of IoT is that it isn’t built with a focus on security, making it highly risky. Pentesting your IoT devices might be the assurance you need. Having a CPENT means that you have an expert who will test your IoT devices and come up with different approaches that a malicious actor can exploit and mitigate them in advance. Likewise, considering that all IoT is different, CPENTs are able to execute thorough and advanced IoT pen-tests to secure your organization.
Which Certification Is Best for Penetration Testing?
Penetration testing jobs are one of the most attractive professions today. This is heightened by the plethora of cyberattacks and the need to test the organization’s systems against the techniques implemented during cyber-attacks by malicious actors. Some of the best penetration testing online certifications include:
EC-Council Certified Penetration Testing Professional (CPENT) Program
The EC-Council’s Certified Penetration tester (CPENT) program gives you the hands-on training you need to know how to execute an efficient penetration test in an enterprise network environment that must be evaded, attacked, defended, and exploited. Likewise, the CPENT Challenge Edition is an affordable learning resource that offers a refresher in subjects such as IoT, binary analysis, SCADA, and ICS. To get details on plans & pricing, enroll now.
EC-Council Licensed Penetration Tester (LPT) Master
The LPT (Master) certification program is the climax to EC-Council’s entire penetration testing training online. Beginning from the Certified Ethical Hacker Program (CEH) to the EC-Council Certified Security Analyst (ECSA) Program, LPT simulates a physical penetration test, accompanied by an additional report to the client. As part of the training process, you are required to execute a full black-box penetration test of a network provided by the EC-Council. For more information, click here.
FAQS
What Is IoT Penetration Testing?
An IoT penetration testing refers to evaluating and exploiting different components available in an IoT device infrastructure to make the device more safe and secure. What you’re doing during an IoT penetration testing is to test the IoT device’s security situation. Although, this would require that the Penetration tester has a proper understanding of the IoT architecture.
What Are Some of the Common Attacks in IoT Systems?
Organizations need to be conscious of the following attacks in IoT systems and use a comprehensive cybersecurity approach to protect themselves. Common attacks in IoT systems include ransomware, botnets, advanced persistent threats, denial of service (DoS) attacks, Distributed Denial of Service (DDoS) attacks, identity and data theft, spamming and phishing, Man-in-the-Middle attacks, Social engineering attacks, and Remote recording.
How Are IoT Devices Hacked?
IoT devices are hacked by malicious hackers who are actively trying to exploit the vulnerabilities within IoT security. Their intent is not to attack the systems themselves. Still, it serves as a starting point for all manner of malicious attacks, including advanced persistent threats, distributed denial-of-service (DDoS) attacks, malware, identity and data theft, social engineering attacks, phishing attacks, etc.
What Are the Top Attack Vectors for IoT Devices?
- HVAC systems
- Programmable logic controllers
- Physical access control solutions
- Network cameras
- Picture archiving and communication systems
- Radiotherapy systems
- Network management cards
- Out-of-band controllers
- Radiology workstations
- Wireless access points