RiSec.Mitch 7 July 2022
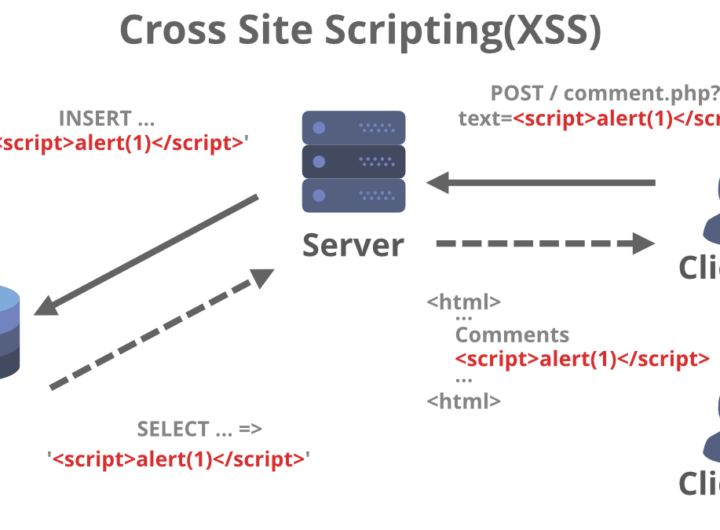
Cross-site scripting is one of the most common and popular web attacks. XSS is a command injection of the client side, it can result in any action that can be performed by the user. Mostly XSS is used for session hijacking where the attacker using javascript makes the victim transmit session cookies to an attacker-controlled server and from there the attacker can perform “session riding”. However, XSS can also result in a complete application takeover. Consider a scenario in which you inject javascript and it gets stored. The admin...