RiSec.n0tst3 16 June 2022
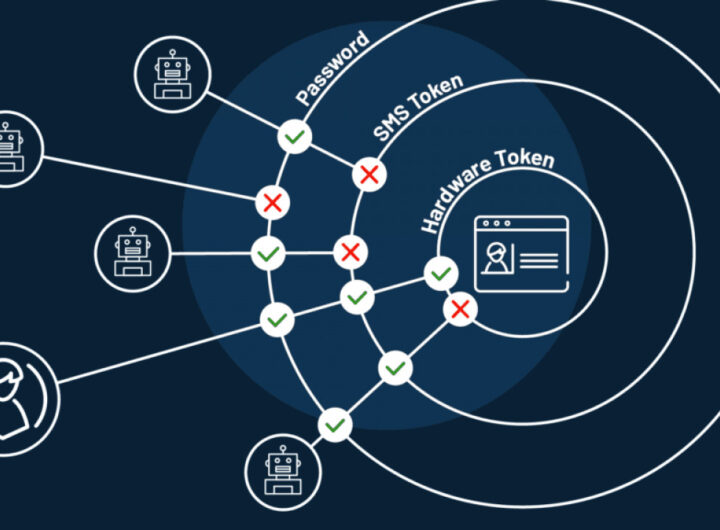
In today’s digital-first landscape, more and more organizations move their workloads to the cloud. However, many do not realize that cloud environments come with a certain set of unique security threats. In this article, you will learn about top cloud application security threats, categorized into three main sources of threats: Attack, misconfiguration and third-party integration. You will also learn four best practices you can use to secure your cloud operations. Top Cloud Application Security Threats Cloud applications include vulnerabilities that on-premises applications do not. For example, built-in internet connectivity can make...