Table of Contents
SearchSploit Guide 2022
InfoSec veteran? novice? confused? It’s a huge acronym.. “InfoSec” CyberSec? regardless, we should all know what Exploit-DB is, exploit-db is a website that provides a collection of several vulnerabilities and code exploits from around the world, otherwise known as PoC (Proof Of Concept) code.
SearchSploit Guide
Exploit-DB is not just a website, there is much more to it than that; Over time, exploit-db developers have created open source tools to facilitate users of all levels, so that the user can easily access the databases without even entering the exploit-db website.
What Is SearchSploit
One of those tools are searchsploit and today we will go over basic setup and usage. Searchsploit gives you the power to perform detailed off-line searches through your locally checked-out copy of the repository. It is an opensource security tool that stores exploit db files locally, so we can easily access exploits in the exploit-db without entering the actual website as we explained earlier
Installation Steps
On Unix systems, everything you need is either “coreutils” or “utilities” (eg bash, sed, grep, awk, etc.), and “git”. It is installed by default on many different Linux distributions, including OS X / MacOS.
If you are not using Kali Linux, the exploitdb package may not be available through the package manager in which case, you can continue to install the searchsploit package using above git command.
Command: apt update && apt -y install exploitdb
If you are using the standard GNOME build of Kali Linux, the “exploitdb” package is already included by default!
- clone project :
git clone https://github.com/offensive-security/exploit-database.git /opt/exploit-database2. Add to path
An optional step that will make using SearchSploit a little easier: is to add it to: $ PATH. :
echo $PATH
/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin3. Next, we’ll use the command below so you can create a symbolic link in the “/ usr / local / bin” directory that points to searchsploit, allowing you to run it without providing the full path.
ln -sf /opt/exploit-database/searchsploit /usr/local/bin/searchsploit4. After completion, It’s time to update SearchSploit:
searchsploit -u5. Install additional modules required to run some functions of searchsploit:
apt install -y libxml2-utils
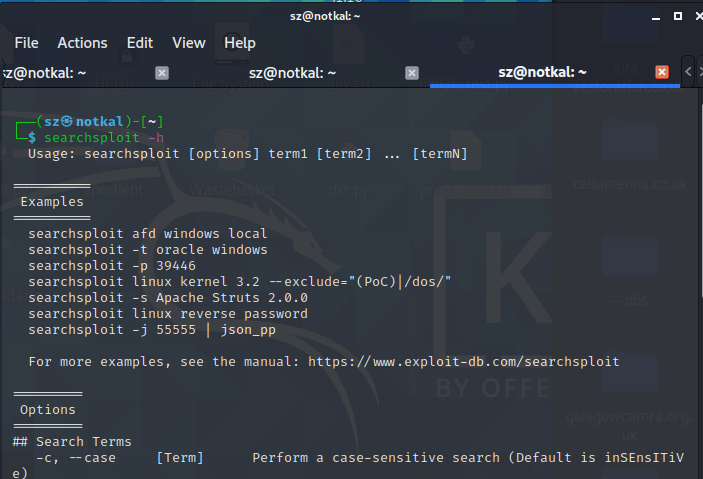
Searchsploit help output
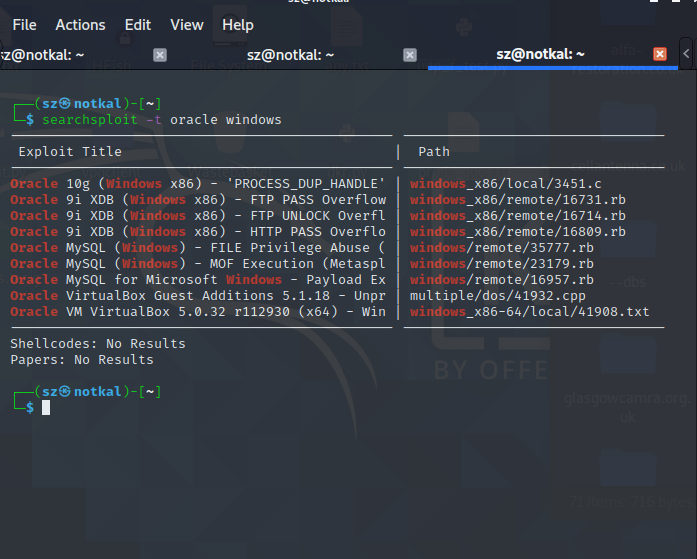
Example search output:
New POC’s, new exploits were released, how do I…
How to update searchsploit?
That’s fairly straightforward, also.
use:
apt update searchsploitor
searchsploit update
Additional Example Usage
==========
Examples
==========
searchsploit afd windows local
searchsploit -t oracle windows
searchsploit -p 39446
searchsploit linux kernel 3.2 --exclude="(PoC)|/dos/"
searchsploit -s Apache Struts 2.0.0
searchsploit linux reverse password
searchsploit -j 55555 | json_ppBasic Searching
Simply add any number of search terms you wish to look for:
--------------------------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
--------------------------------------------------------------------------------------- ---------------------------------
Microsoft Windows (x86) - 'afd.sys' Local Privilege Escalation (MS11-046) | windows_x86/local/40564.c
Microsoft Windows - 'afd.sys' Local Kernel (PoC) (MS11-046) | windows/dos/18755.c
Microsoft Windows - 'AfdJoinLeaf' Local Privilege Escalation (MS11-080) (Metasploit) | windows/local/21844.rb
Microsoft Windows 7 (x64) - 'afd.sys' Dangling Pointer Privilege Escalation (MS14-040) | windows_x86-64/local/39525.py
Microsoft Windows 7 (x86) - 'afd.sys' Dangling Pointer Privilege Escalation (MS14-040) | windows_x86/local/39446.py
Microsoft Windows XP - 'afd.sys' Local Kernel Denial of Service | windows/dos/17133.c
Microsoft Windows XP/2003 - 'afd.sys' Local Privilege Escalation (K-plugin) (MS08-066) | windows/local/6757.txt
Microsoft Windows XP/2003 - 'afd.sys' Local Privilege Escalation (MS11-080) | windows/local/18176.py
--------------------------------------------------------------------------------------- ---------------------------------
Shellcodes: No Result
kali@kali:~$kali@kali:~$ searchsploit afd windows localNote, SearchSploit uses an AND operator, not an OR operator. The more terms that are used, the more the results will be filtered out.
Elite Tip: Do not use abbreviations (use SQL Injection, not SQLi).
Elite Tip If you are not receiving the expected results, try searching more broadly by using more general terms (use Kernel 2.6 or Kernel 2.x, not Kernel 2.6.25).
Title Searching
By default, searchsploit will check BOTH the title of the exploit as well as the path. Depending on the search criteria, this may bring up false positives (especially when searching for terms that match platforms and version numbers). Searches can be restricted to the titles by using the -t option:
kali@kali:~$ searchsploit -t oracle windows
--------------------------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
--------------------------------------------------------------------------------------- ---------------------------------
Oracle 10g (Windows x86) - 'PROCESS_DUP_HANDLE' Local Privilege Escalation | windows_x86/local/3451.c
Oracle 9i XDB (Windows x86) - FTP PASS Overflow (Metasploit) | windows_x86/remote/16731.rb
Oracle 9i XDB (Windows x86) - FTP UNLOCK Overflow (Metasploit) | windows_x86/remote/16714.rb
Oracle 9i XDB (Windows x86) - HTTP PASS Overflow (Metasploit) | windows_x86/remote/16809.rb
Oracle MySQL (Windows) - FILE Privilege Abuse (Metasploit) | windows/remote/35777.rb
Oracle MySQL (Windows) - MOF Execution (Metasploit) | windows/remote/23179.rb
Oracle MySQL for Microsoft Windows - Payload Execution (Metasploit) | windows/remote/16957.rb
Oracle VirtualBox Guest Additions 5.1.18 - Unprivileged Windows User-Mode Guest Code Do| multiple/dos/41932.cpp
Oracle VM VirtualBox 5.0.32 r112930 (x64) - Windows Process COM Injection Privilege Esc| windows_x86-64/local/41908.txt
--------------------------------------------------------------------------------------- ---------------------------------
Shellcodes: No Result
kali@kali:~$
kali@kali:~$ searchsploit oracle windows | wc -l
100
kali@kali:~$If we did not use -t, we would have 94 (6 lines are in the heading/footer) results, rather than 9.
Removing Unwanted Results
you can remove unwanted results by using the --exclude option. We are also able to remove multiple terms by separating the value with a | (pipe).
Elite Tip: By doing: searchsploit linux kernel --exclude="(PoC)|/dos/" | grep ' 3.2', you’ll get an even “cleaner” output (sorted based on the version without any heading/footers).
Examining Nmap result
Nmap has a feature that let you save its output result in .xml format and we can identify each exploit associated with the Nmap XML file.
Nmap -Pn -n IP -oX output.xmlWith the help of above command, we have saved the scanning result of Nmap in an XML file, so that we can search the exploit related to scanned port/services.
searchsploit -x --nmap output.xmlExamine an Exploit
Using —examine option enables examine parameter to read the functionality of that exploit with the help of $PAGER.
searchsploit 9542 --examineWe shall leave it there, for now.
Be sure to check more of our guides! Cybersecuirty is always the topic. we’re working on further enhancing the academy.
Suggest a change to this article
Go to Cybersecurity Knowledge Base
Got to the Latest Cybersecurity News
Stay informed of the latest Cybersecurity trends, threats and developments. Sign up for our Weekly Cybersecurity Newsletter Today.
Remember, CyberSecurity Starts With You!
- Globally, 30,000 websites are hacked daily.
- 64% of companies worldwide have experienced at least one form of a cyber attack.
- There were 20M breached records in March 2021.
- In 2020, ransomware cases grew by 150%.
- Email is responsible for around 94% of all malware.
- Every 39 seconds, there is a new attack somewhere on the web.
- An average of around 24,000 malicious mobile apps are blocked daily on the internet.
1,675 total views, 3 views today