
north korean hacking group
A North Korean cyberespionage group named Konni has been linked to a series of targeted attacks aimed at the Russian Foreign Ministry of Affairs (MID) with New Year lures to compromise Windows systems with malware.
North Korean Hackers Start New Year with Attacks on Russian Foreign Ministry
“This activity cluster demonstrates the patient and persistent nature of advanced actors in waging multi-phased campaigns against perceived high-value networks,” researchers from Lumen Technologies’ Black Lotus Labs said in an analysis shared with The Hacker News.
The Konni group’s tactics, techniques, and procedures (TTPs) are known to overlap with threat actors belonging to the broader Kimsuky umbrella, which is also tracked by the cybersecurity community under the monikers Velvet Chollima, ITG16, Black Banshee, and Thallium.
The most recent attacks involved the actor gaining access to the target networks through stolen credentials, exploiting the foothold to load malware for intelligence gathering purposes, with early signs of the activity documented by MalwareBytes as far back as July 2021.
Subsequent iterations of the phishing campaign are believed to have unfolded in three waves — the first commencing on October 19, 2021 to harvest credentials from MID personnel, followed by leveraging COVID-19 themed lures in November to install a rogue version of the Russian-mandated vaccination registration software that served as a loader for additional payloads.
“The timing of this activity closely aligned with the passage of Russian Vaccine Passport laws that mandated Russians had to receive a QR code from the government to prove vaccination in order to access public places such as restaurants and bars,” the researchers noted.
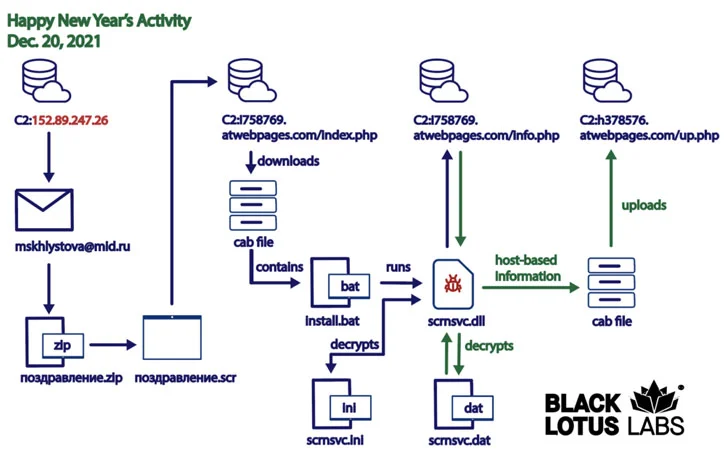
The third attack, also corroborated by Cluster25 earlier this week, began on December 20, 2021, using New Year’s Eve festivities as a spear-phishing theme to trigger a multi-stage infection chain that culminated in the installation of a remote access trojan named Konni RAT.
Specifically, the intrusions transpired by first compromising the email account belonging to a staff member of the MID, from which emails were sent to at least two other MID entities, including the Russian Embassy in Indonesia and Sergey Alexeyevich Ryabkov, a deputy minister overseeing non-proliferation and arms control.
The email missives seemingly propagated a “Happy New Year’s” message, only to contain a trojanized screensaver attachment that’s designed to retrieve and run next-stage executables from a remote server. The final stage of the attack is the deployment of the Konni RAT trojan, which conducts reconnaissance of the infected machine and exfiltrates the collected information back to the server.
“While this particular campaign was highly targeted, it is vital for defenders to understand the evolving capabilities of advanced actors to achieve infection of coveted targets,” the researcher said, urging organizations to watch out for phishing emails and use multi-factor authentication to secure accounts.
You may also enjoy reading, Assange Wins First Stage in Effort to Appeal US Extradition
Stay informed of the latest Cybersecurity trends, threats and developments. Sign up for RiSec Weekly Cybersecurity Newsletter Today
Remember, CyberSecurity Starts With You!
- Globally, 30,000 websites are hacked daily.
- 64% of companies worldwide have experienced at least one form of a cyber attack.
- There were 20M breached records in March 2021.
- In 2020, ransomware cases grew by 150%.
- Email is responsible for around 94% of all malware.
- Every 39 seconds, there is a new attack somewhere on the web.
- An average of around 24,000 malicious mobile apps are blocked daily on the internet.
33,741 total views, 2 views today





1 thought on “North Korean Hacking Group Target Russian Foreign Ministry”