New Cybersecuirty Articles
Cybersecurity News
Look no further! We have a selection of handcrafted, handpicked cybersecurity news articles and related resources. We provide independent research and analysis in a wide range of sectors. What about infosec? Well, we cover that too, obviously.
Cybersecurity Tutorials
Additionally, we have started to serve a CyberSecurity Academy archive which will be home to unique write-ups and some of the Internet’s top tutorials. Don’t forget, Cybersecurity starts with you.
Active Cyber Threats in the wild
At real Infosecurity we endeavour to cover active threats in the wild and help you secure what is important to you, empowering you to advance your cyber knowledge.
Submit an article
Maybe you have a cybersecurity news article you’d like to submit to us? You can do that through the contact page.
New cybersecurity articles
Want to keep up-to-date with our new cybersecurity articles? Our Weekly Cybersecurity Newsletter has a wide range of topics in the new cybersecurity sphere covered. Our new cybersecurity articles include emerging developing threats, data breaches and malware news & analysis and lots more.
Feel like we are missing a specific topic? feel feel to contact us with your cybersecurity related input. We’d love to hear from you.
What really is Cybersecurity ?
The act of defending computers, servers, mobile devices, electronic systems, networks and data from malicious attacks which range from business organisations to personal devices.
Network security and application security focuses on securing computer networks, along with software and device free from threats and vulnerabilities, respectively.
the state of being protected against the criminal or unauthorized use of electronic data, or the measures taken to achieve this.
TLDR
Cybersecurity Academy Cybersecurity News Data Breach News Data Security Featured How to Kali Linux Guides & Tools | Cybersecurity Academy Tools Trending Vulnerabilities World Affairs
Google Improves Password Manager to Boost Security
26,020 total views
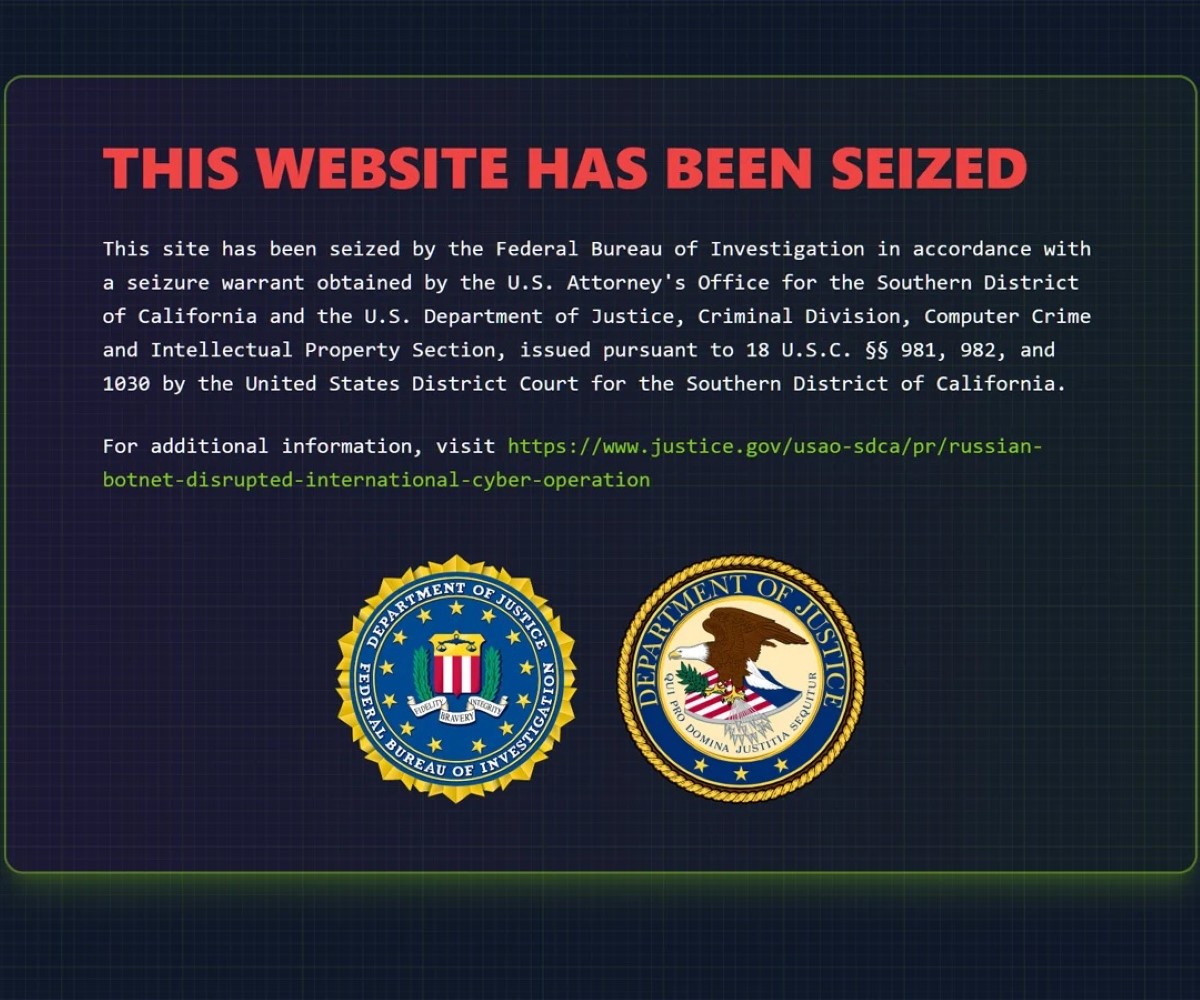
Meet the Admins of the RSOCKS Proxy Botnet
22,738 total views
Cloud Application Security Best Practices
28,470 total views
Debian: DSA-5163-1: Chromium Security update
102,096 total views
What Is a CVE? Common Vulnerabilities and Exposures Explained
40,344 total views, 3 views today
How Google Works
8,006 total views
How the metaverse could shape cybersecurity in 2022
26,781 total views