How To Fix Apache Cassandra RCE:
The security research team from JFrog uncovered a remote code execution vulnerability in Apache Cassandra. The flaw is tracked under the CVE ID ‘CVE-2021-44521’ is assigned a base score of 8.4 allows attackers to perform remote code execution vulnerability on affected versions of Apache Cassandra database software. Since the vulnerability is easy to exploit and has the potential to wreak havoc on systems, it is very important to fix the CVE-2021-44521 vulnerability.
If you are using Cassandra database in any of your DevOps projects, please read this post. We have published this blog post to let you know how to fix the Apache Cassandra RCE vulnerability and how to mitigate the flaw in the case of being unable to apply the permanent fix.
Before we jump into the topic, it is necessary to understand certain aspects to learn about the flaw. Let’s get started.
What Is Apache Cassandra?
Apache Cassandra is a well-known NoSQL database developed in Java. Its Scalability and distributed nature made it extremely popular. Companies like Netflix, Twitter, Urban Airship, Constant Contact, Reddit, Cisco, OpenX, Digg, CloudKick, Ooyala, etc., will use this database extensively in their development projects. Its distributed nature made it more popular in DevOps and cloud-native development landscape. A well-known cloud-based turnkey solution DataStax (a serverless, multi-cloud DBaaS) is built on Cassandra.
What Is Nashorn Engine?
Since Cassandra is a NoSQL database, it stores data in JSON files. It uses User-Defined-Functions (UDFs) (written in Java and JavaScrip) to perform custom processing of data in the database. Nashorn is a JavaScript Engine that runs on top of the JVM, used to interpret UDFs written in JavaScripts.
Cassandra wrapped the Nashorn Engine with is a SandBox making Nashorn execution more secure. Or else anyone can abuse Nashorn by sending malicious untrusted code or UDFs.
How An Attacker Exploits Apache Cassandra RCE Vulnerability- CVE-2021-44521?
Report says that Attackers could exploit the Nashorn engine only with this non-default configuration set in the cassandra.yaml configuration file. Use your choice of text editor to edit the ‘/etc/cassandra/cassandra.yaml’ file.
$ sudo nano /etc/cassandra/cassandra.yaml# Enable UDF support for both Java and JavaScript
enable_user_defined_functions: true
enable_scripted_user_defined_functions: true
# This is the key for the exploitation of CVE-2021-44521. It's default value is 'true'.
# true == Each invoked UDF function will run in a different thread, with a security manager without any permissions. Thsi lead to DoS attack.
# false == All invoked UDF functions run in the Cassandra daemon thread, which has a security manager with some permissions. This lead to SandBox escape and RCE.
enable_user_defined_functions_threads: falseWhen the flag enable_user_defined_functions_threads in cassandra.yaml file is set to false, attackers canescape the sandbox and achieve remote code execution.
Note: These flags can also be configured via the Config.java configuration file.
About the enable_user_defined_functions_threads Flag.
This is the key to the exploitation of CVE-2021-44521.
It’s default value is ‘true’.true == Each invoked UDF function will run in a different thread, with a security manager without any permissions. This will lead to a DoS attack.false == All invoked UDF functions run in the Cassandra daemon thread, which has a security manager with some permissions. This will lead to SandBox escape and RCE.
JFrog Security team says that “enable_user_defined_functions_threads is set to true by default, which means each invoked UDF function will run in a different thread, with a security manager without any permissions. This enables a malicious user to create a UDF that will shut down the Cassandra daemon. This is due to the behavior of the UDF timeout mechanism, governed by the user_defined_function_fail_timeout flag.
If a UDF function runs more than the allotted time, the entire Cassandra daemon will shut down. An attacker can easily DoS the entire database by creating a function which loops forever with while(true).
PoC Of Apache Cassandra RCE Vulnerability- CVE-2021-44521:
Kaspi published a PoC in the blog post. The researcher showed how a file named “hacked” is created on the Cassandra server.
How To Fix Apache Cassandra RCE Vulnerability- CVE-2021-44521?
Cassandra database addressed this vulnerability by adding a new flag allow_extra_insecure_udfs in v3.0.26, v3.11.12, and v4.0.2.
The flag allow_extra_insecure_udfs is set false by default, which prevent turning off the security manager and blocks UDFs to interact with elements outside the sandbox.
We recommend users of Apache Cassandra to upgrade to one of the following versions.
- 3.0.x users should upgrade to 3.0.26
- 3.11.x users should upgrade to 3.11.12
- 4.0.x users should upgrade to 4.0.2
How to upgrade Apache Cassandra on Linux?
There are a few simple prerequisites before upgrading Apache Cassandra database:
1. Take the system snapshot backup.
2. Remove all dead nodes.
3. Do not run nodetool repair or other tasks.
- Flush all memtables from the nodeRun nodetool drain command before shut down the Cassandra service. This command will help in achieving these:
1. Flush all memtables from the node to SSTables on disk.
2. Stops listening for connections from the client and other nodes.
3. Prevents overcounts of counter data, and speeds up restart post-upgrade.
$ sudo nodetool drain -h hostname- Stop Cassandra services.
$ sudo systemctl status cassandra
Back up your Cassandra configuration files
Use this command to take the backup of cassandra.yaml
$ sudo cp /etc/cassandra/cassandra.yaml /etc/cassandra/cassandra.yaml.backup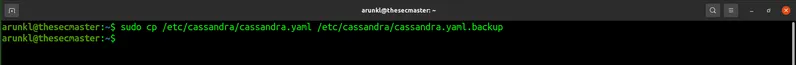
Install Java 8
Since Java 8 is the recommended version it is good to install Java 8 or set Java 8 as the default Java version.
Commands to install the Java 8 and set it as default version:
$ sudo apt-get update
$ sudo apt-get install oracle-java8-set-default
$ sudo java -version- If you already have Java 8 want to set it as default version. Run this command:
$ sudo update-alternatives –config java- Install the new version of Apache Cassandra$ sudo apt-get update:
$ sudo apt-get install cassandra=3.11.12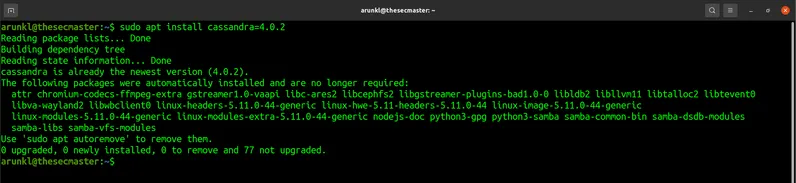
- Check the services and start if not active and running
Commands to start | stop | restart | status Apache Cassandra database:
$ sudo systemctl status cassandra
$ sudo systemctl start cassandra
$ sudo systemctl stop cassandra
$ sudo systemctl restart cassandra
Check the logs for any issues:
$ tail -f /ttio/var/logs/cassandra/system.log
- Run nodetool upgradesstables
$ sudo nodetool upgradesstables- Check the logs for any issues
$ tail -f /ttio/var/logs/cassandra/system.log
- Check the status of the cluster
$ nodetool -h hostname status
How to Mitigate Apache Cassandra RCE Vulnerability- CVE-2021-44521?
The vendor has recommended a few mitigations techniques for those who can’t apply the permanent patch soon.
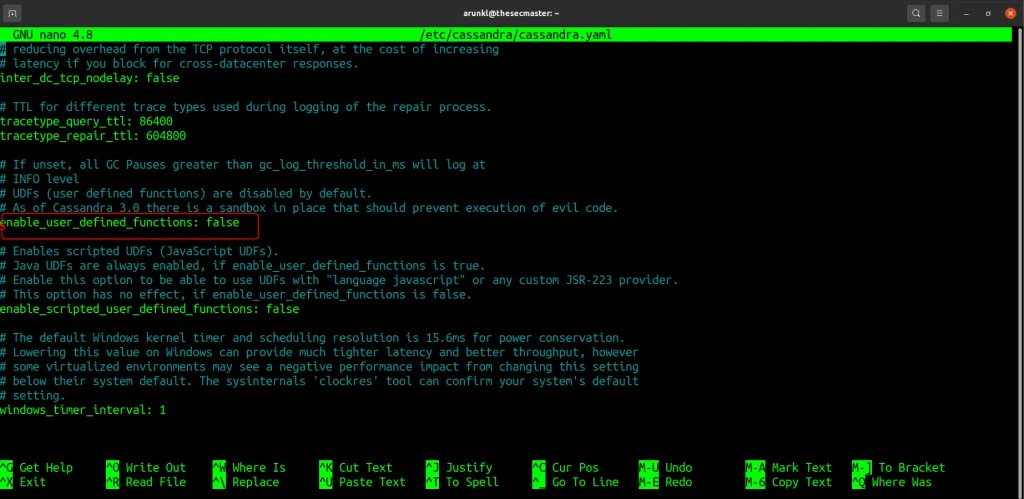
- If you are not using UDFs in your deployment, set these flags;
- Set the flag enable_user_defined_functions to false to disable the UDF completely.
- Set enable_user_defined_functions_threads to true if UDFs are needed.
- Removing the following permissions: ALL FUNCTIONS, ALL FUNCTIONS IN KEYSPACE and FUNCTION for CREATE, ALTER and EXECUTE queries to remove the permissions of creating, altering and executing functions for untrusted users.
Conclusion
We hope this post will help you know How to Fix Apache Cassandra RCE Vulnerability- CVE-2021-44521. Thanks for reading this threat post. Please share this post and help to secure the digital world.
You may also enjoy reading, CVEs You May Have Missed While Log4J Stole The Headlines
Stay informed of the latest Cybersecurity trends, threats and developments. Sign up for RiSec Weekly Cybersecurity Newsletter Today
Remember, CyberSecurity Starts With You!
- Globally, 30,000 websites are hacked daily.
- 64% of companies worldwide have experienced at least one form of a cyber attack.
- There were 20M breached records in March 2021.
- In 2020, ransomware cases grew by 150%.
- Email is responsible for around 94% of all malware.
- Every 39 seconds, there is a new attack somewhere on the web.
- An average of around 24,000 malicious mobile apps are blocked daily on the internet.




